I wanted to title this “IPv6 still not viable” but really this is a complex problem of spam, my hosting provider Linode, Comcast, and Spamhaus.
My hosting provider supplies both IPv4 and IPv6 on every machine I spin up. That was fine, until it wasn’t.
I run my own mail server. I’ve been doing SMTP mail for twenty years (more, really) and I am careful to not let anyone randomly relay through my server. I even had to shut down comments on this blog because script kiddies were abusing the new-user-signup process to annoy random people with new-user-spam emails. That was months ago.
I’ve done my due diligence and have SPF and DKIM set correctly. I regularly check with https://www.mail-tester.com/ to make sure everything is still good, and I routinely get a score of 10 out of 10.
Yet, recently Comcast has been refusing to send my email to my friends, because of Spamhaus. Spamhaus says the IPv6 range I am in is populated by spammers.
Linode must have (or had) a customer who was a spammer in the same data center I was in. So in a large part, my problem stems from Linode. I can understand that Linode might have a new customer who tried setting up a mail server, botched the anti-spam part of it, and legitimately got put on an anti-spam list or twenty, including Spamhaus.
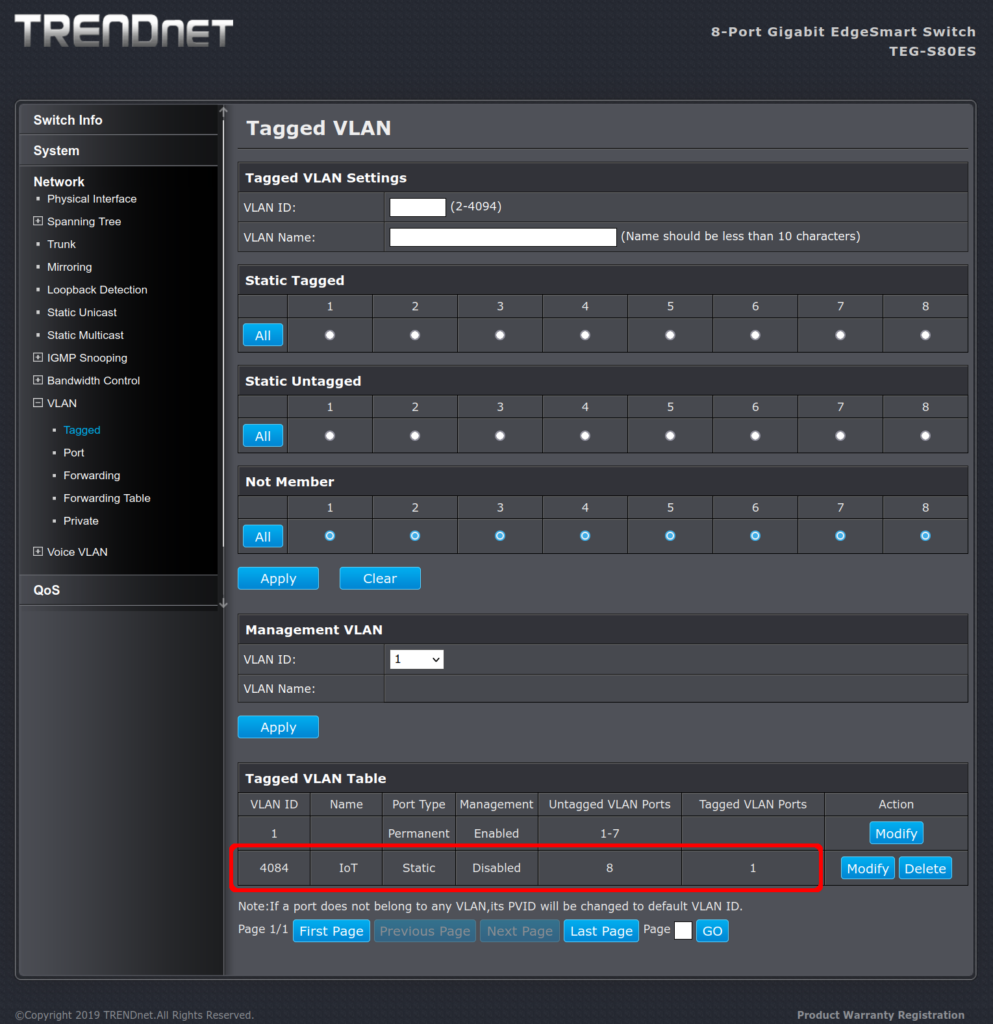
Apparently, Linode puts everyone in a data center in the same huge IPv6 range using something called SLAAC. There are Linode community posts going back nine years about Comcast blocking email because Spamhaus and Linode cannot agree on the correct sizing of a customer’s address space within a SLAAC addressed network.
Spamhaus refuses to pick and choose which addresses in the range are violators – it just blocks the whole range.
So I am getting blocked by neighborhood association.
I don’t know if this is Linode’s fault for making the range too large, or Spamhaus’ fault for not being granular. Or if it is Linode’s fault for not policing the spam behavior of its customers. No matter: I can’t email my volunteer service friends the monthly reports, meeting minutes, or even personal email if the email goes out over the IPv6 address.
So the IPv6 network had to go.
It is done.
And it was not easy. My mail host now whines about not being able to get Ubuntu updates. I want to move it to Debian anyway, but this rushes that project.
And here on my home network, things really didn’t work right, with IPv6 present here but not working on the mail server out in Linode lan(d). Thunderbird was throwing a hissy fit for a few days. So then I had to reconfigure everything here at home to be IPv4 only. That was a lot of work.
But at least at the end of it, if a service like Comcast (or anyone else) puts me on an anti-spam list, I’ll only have the single IPv4 address to get unblocked.
I kind of feel bad. I have a friend who is a huge proponent of IPv6, and he now works for Google, and probably one of the things that got him hired was the advocacy work he did for this cause. And I like the idea of IPv6.
Here’s a mild tangent: way back when, Novell had a networking technology called IPX/SPX. For addressing, it used a 32 bit chunk concatenated with a 48 bit chunk: the first 32 bits were the network address and the last bits were from the machine’s MAC address. On local networks, it was speedy, and didn’t use a lot of memory, which is why many LAN games ran over it. Some of my most fun ever was playing Command & Conquer: Generals with my sons over IPX/SPX.
As the Internet was taking off, it was clear that TCP/IP in IPv4 was the way everyone was connecting their local network to the Internet. IPv4 could do NAT (network address translation). In fact, it required address resolution protocol (ARP), which made it slower than IPX/SPX. Some people at Novell went to some working group, and suggested that the Internet could carry IPX/SPX traffic too: they got laughed at. “No, we’re not going to add IPX/SPX to the Internet”. (The NAT problem was solved in IPX/SPX networks with gateways).
Anyway … care to guess what the IPv6 address space is? Could it happen to be 64 bits for the network address and 64 bits from the machine’s MAC address?
Yes, as a matter of fact in substantial ways, IPv6 is IPX/SPX grown to 128 bits. And people like it because it is speedy. Everything old is new again.